One of the questions we get asked a lot when it comes to GDPR is:
“Do I need to encrypt my emails to be GDPR compliant?”
All businesses communicate via email. It could be with partners, suppliers, customers, or other stakeholders.However, just like the 'old-fashioned' method of a letter sent in the post, anyone can read the contents of an email if it's sent to the wrong person or intercepted along the way.An unencrypted email is open to interception, leaving all information within at risk.Depending on what's being sent, this could include names and email addresses, medical information, finances, and more. All very tempting to malicious actors, unintended recipients, and cybercriminals.That's why email encryption is considered to be highly valuable under the General Data Protection Regulation (GDPR).
GDPR Compliance
Before we consider encryption, a quick word on compliance. In fact, a whole article -> GDPR: Compliant or not compliant?This piece discusses the notion of “compliance” and what it actually means. It’s worthwhile understanding this before diving into specific technologies like encryption.
Non-Prescriptive
None of the following laws, regulations or standards is prescriptive about data security or email encryption:
- 1998 Data Protection Act (DPA)
- General Data Protection Regulation (GDPR)
- ISO27001:2013
If you take a look at what the Information Commissioner’s Office (ICO) says on data security (you can find it here). It says a couple of pertinent things:
“you should have security that is appropriate to: the nature of the information in question; and the harm that might result from its improper use, or from its accidental loss or destruction.”
“The Act does not require you to have state-of-the-art security technology to protect the personal data you hold, but you should regularly review your security arrangements as technology advances.”
If you (as we have) go through ISO27001 certification there are no prescriptive statements about technology or indeed email encryption. In fact, much of the standard relates to people (likely to be your greatest security weakness) and the policies that you put in place to ensure that they uphold the security of your data. Where it does touch on “technology” - it mostly (but not exclusively) relates to the disposal of IT equipment and portable storage devices (like USB sticks). Possibly the two single biggest causes of privacy breaches.So, no matter what Joe Bloggs states (with gusto) on your favourite Facebook group there is no mandatory or legal requirement for you to encrypt your emails. But that doesn’t mean you shouldn’t consider it.
Appropriate
One of the critical words used in the DPA and GDPR is “appropriate”. Rightly or wrongly, this means that there are no defined rules and you need to make a judgement on what security measures you believe are sensible for your practice. Why? Because the DPA/GDPR are “one-size fits all” pieces of legislation and it would be impossible to define cast iron requirements for every business type/size and privacy scenario.In my humble opinion if you’re running a small/medium-sized healthcare practice and you’re considering what data security measures are “appropriate” you need to consider your risks in light of:
- Nature of personal information being held or transmitted - if you don’t transmit any, there’s no risk or if you only transmit a name and DoB this is materially less sensitive than say a psychological diagnosis relating to a specific named client
- Size of your organisation - if you’re two people there are potentially fewer risks to manage or control than if you employ 5000 people
- Employment model - if you employ temporary part-time staff you “might” take a different view to one where your practice is owned and run by three shareholding partners, for example
- Employment contracts - this is rather a negative perspective but the robustness of your employment contracts might inadvertently contribute to poor data security. Staff might do an extra check when sending an email if they understand that a data breach would be viewed as gross misconduct
- Who you’re sending information to - whilst it might seem “helpful or more personal” to include a client’s name in communications there’s no need to do so if the recipient can lookup a patient's details using a unique, non-identifiable ID like NHS number or equivalent
- Systems being used - are you using your own systems, under your own control, or are you using a third-parties network/infrastructure/email?
- Are systems “business only” or are they split between personal and business use. I’ve certainly come across a number of smaller practices who run their clinic appointments in Apple Calendar on their iPhone alongside their personal contacts etc. Again, you might take the view that this lack of separation presents a potential risk
Also, keep in mind that the “appropriateness” of your measures will only be brought into question in the event of a breach. I don’t for one second suggest that you should view this as a positive. But, what I’m saying is that you should “stress test” your appropriateness rationale and make sure that it stands up to logical scrutiny in the event that you do experience a data breach.
Email Encryption
Unfortunately, there’s a bit of confusion about what email encryption is and where it applies. Hopefully, I can de-mystify things a bit…Just like WriteUpp, all of the mainstream email providers (GMail, Hotmail, Apple Mail) are encrypted using HTTPS. In essence, this means that if someone were to intercept the network traffic being sent by your email service they would NOT be able to read your emails. If you’re not familiar with HTTPS and SSL the following article explains this in more detail:HTTPS - What is it and why is it important?“End to end encryption” on the other hand is something different. With end-to-end email encryption every message you send is encrypted with a unique password/key, which the sender must define when they create the message and the recipient must enter/provide before they can open/read the message.Here’s what you might see in your inbox if you receive an encrypted message:
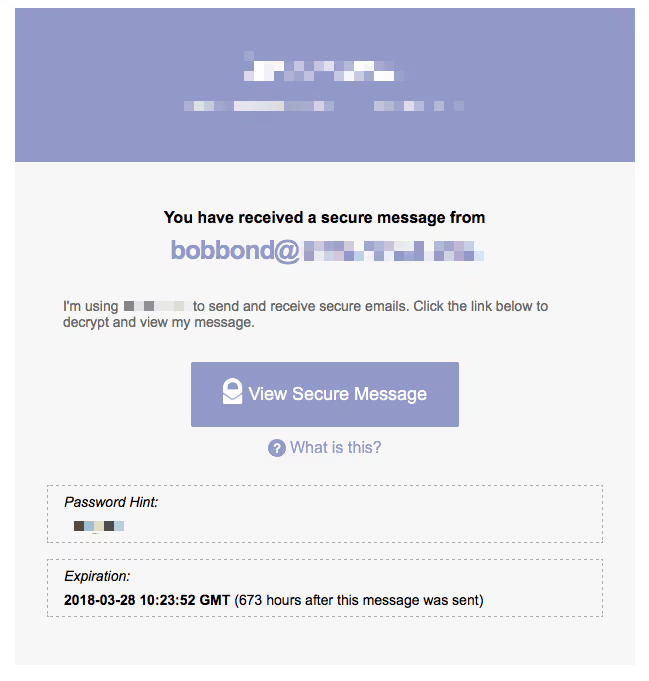
At this point, if you wish to open the message you need to enter the password:
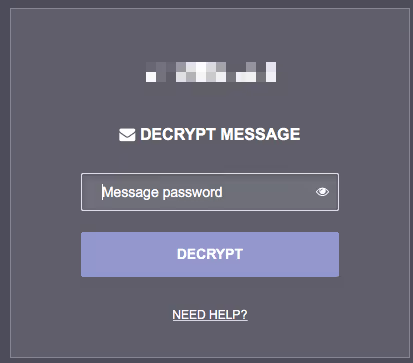
All good and secure. But….how do you get the password to the recipient?
- Phone - time consuming
- Same password every time (assuming you’ve agreed one) - kinda defeats the object
- Email - kinda defeats the object
- Text/SMS - time consuming
Alternatively, you’ll need to convince everyone that you send emails to that they should set up an encrypted email account with your chosen provider.There are other slightly different models where the recipient needs to install an applet before they can read the message but in all cases the tech is the same. At the sender end there is an encryption mechanism and necessarily at the receiver end there needs to a decryption mechanism (password, applet etc.)This might all seem very negative and I don’t mean it to be, but encrypted email has been around for a long time (it’s definitely not new!) and there’s a reason that uptake has been relatively low.On the flipside encrypting an email in this way will deal with the situation where you accidentally send an email to the wrong recipient. Some might also suggest that email encryption is beneficial in the event that your email account is hacked but in this day and age with facial/fingerprint recognition and two-factor authentication there’s really no excuse for not securing your email account properly.
Risk & Prevention
Which brings us neatly back to “appropriateness”. How big is the risk and what actions do you take to mitigate it?If you feel that there is a risk that you might send an important document containing sensitive personal information to the wrong email recipient then encryption may be a measure that you need to consider.But there are alternate (and potentially simpler) strategies that could help you avoid these sorts of “fat finger” issues, such as:
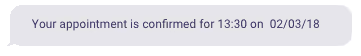
- Not including any PII (Patient Identifiable Information) in confirmation/reminder communications. It might seem more friendly and personable to include lots of information in your comms but sticking to the bare minimum negates risk, see below:
- Modifying your document/report templates so that they ONLY include unique identifiers to your client, such as NHS Number (UK), CPR Number (Denmark) etc and the WUID (WriteUpp ID) or whatever internal ID your system uses, see below:
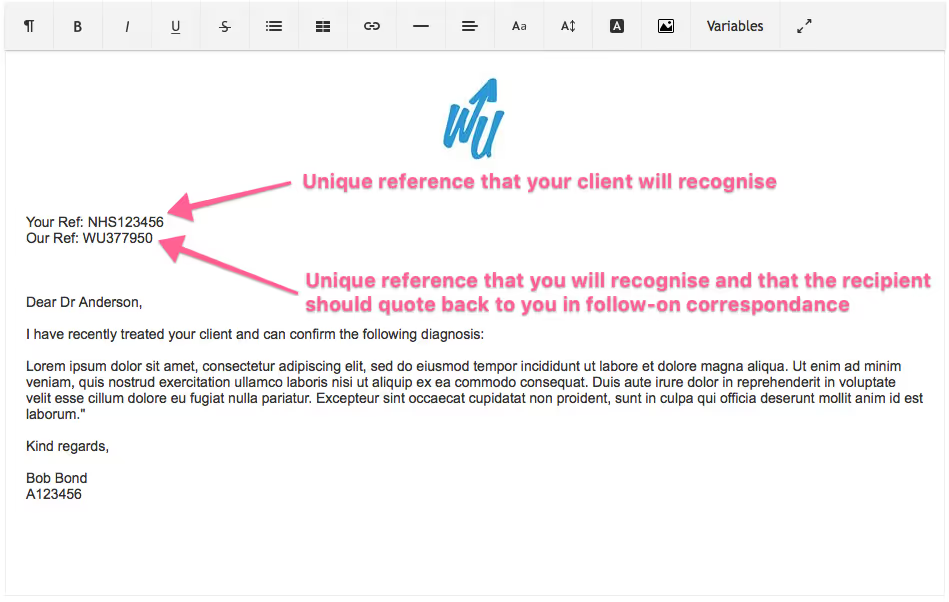
- In the example above this assumes that the receiving organisation has access to look-up an NHS Number or equivalent. But, keep in mind that whoever you are sending content to also needs to comply with GDPR so taking a more minimalist (non PII) approach should benefit both you and the recipient. You just need to agree on a protocol for communications.
Encryption is a tactical solution but not THE solution
Keep in mind that data leaks aren’t restricted to email. In fact, ask yourself when you last sent a critical email to the wrong person?By way of a alternate example, consider a scenario where you have a multi-disciplinary team session and mark up patient names on a whiteboard in a meeting room. It’s easy enough for the cleaner, security guards to see this information if it isn’t anonymised (or wiped).The point is that email encryption is a very specific technology that will help resolve a very specific issue (or set of issues). Technology alone never solves these sorts of problems because as I mentioned earlier human beings are always the greatest weakness when it comes to data security.The solution in my humble opinion is to adjust your culture and thinking to reduce the amount of unnecessary transmission of personal information, which immediately eradicates your data risk. Sure, there may be situations where you absolutely NEED to transmit sensitive personal information and in these situations email encryption is definitely an appropriate measure but its not the silver bullet that some might be suggesting.



Join over 50,000 clinicians that we've helped using WriteUpp
Start my free trial



